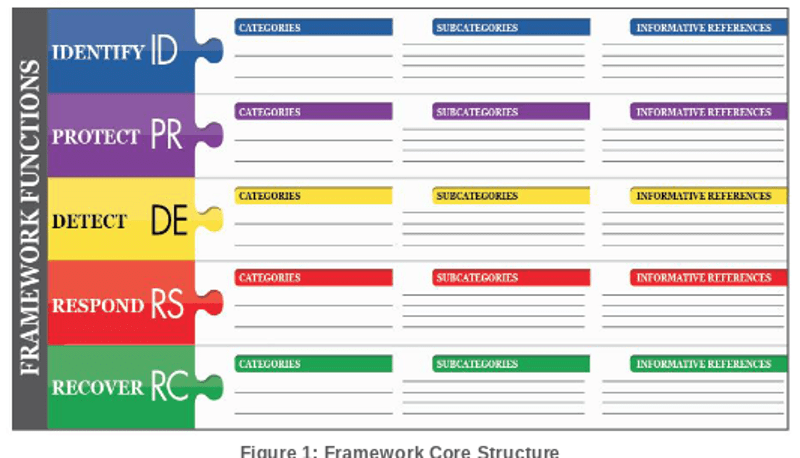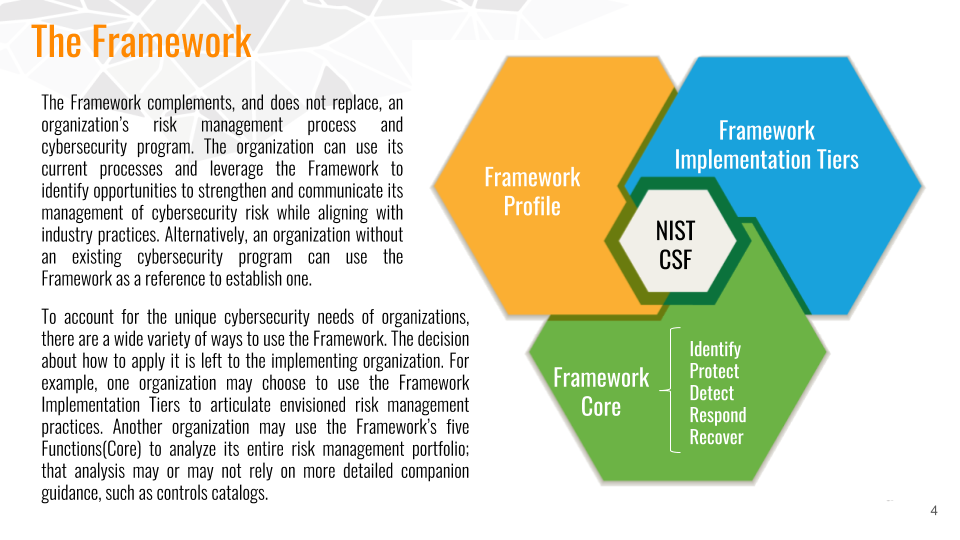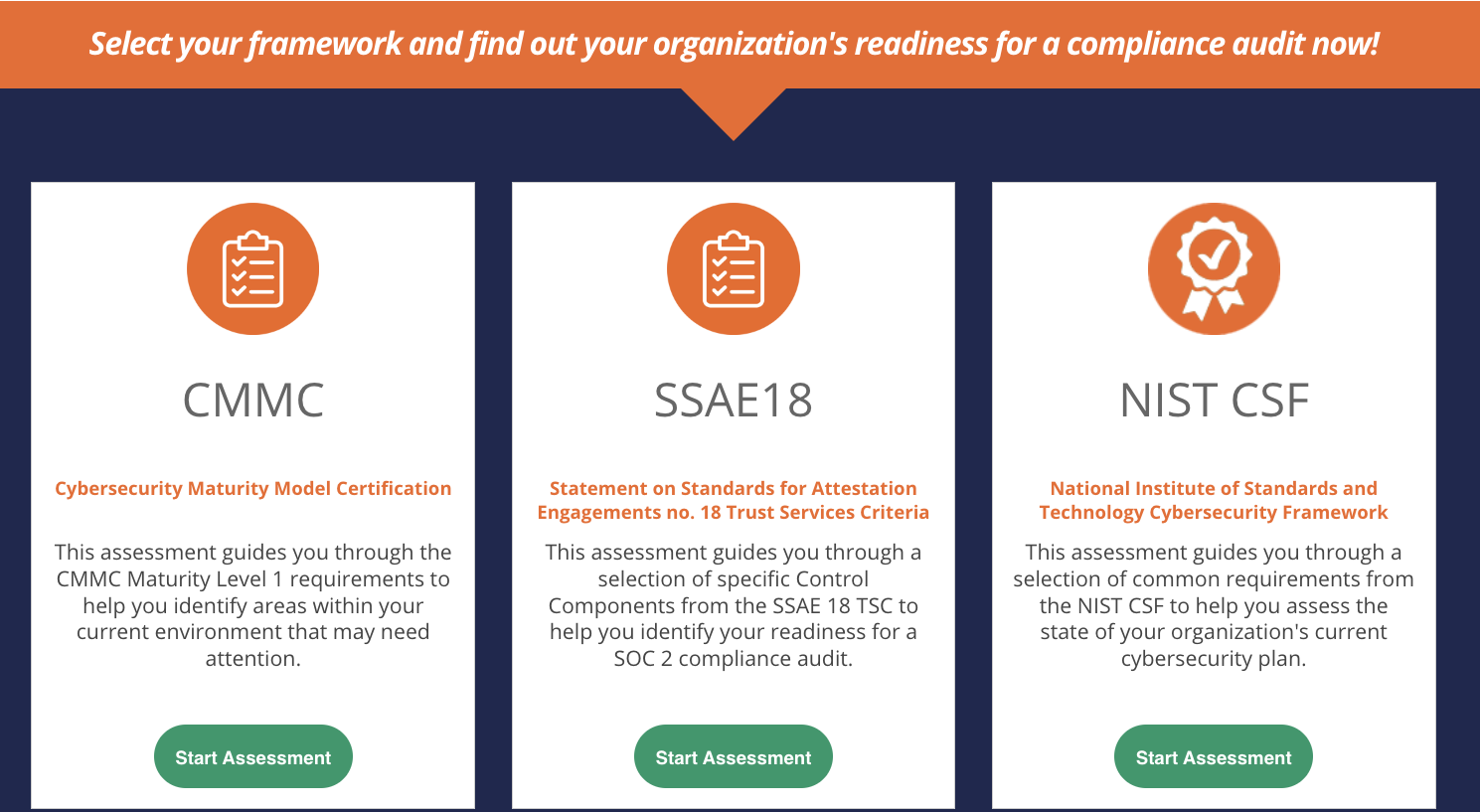
KnowBe4's Compliance Audit Readiness Assessment (CARA) Now Maps to the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF)

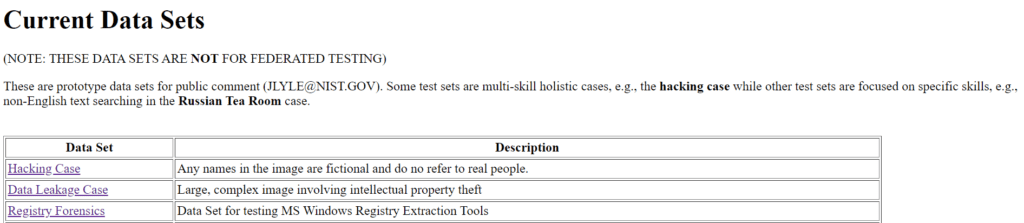
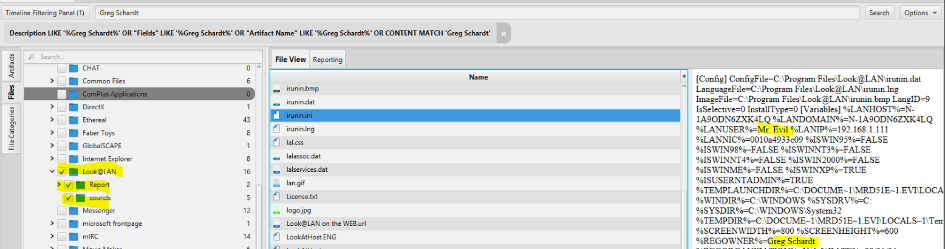
CHFI v10 – Bài Thực Hành Pháp Y Số Hacking Case NIST Với FTK Imager , Regstry Viewer hoặc Autopsy – học an toàn & bảo mật thông tin