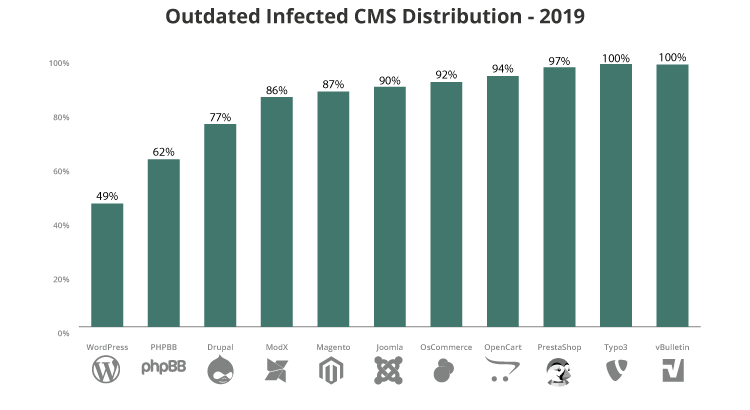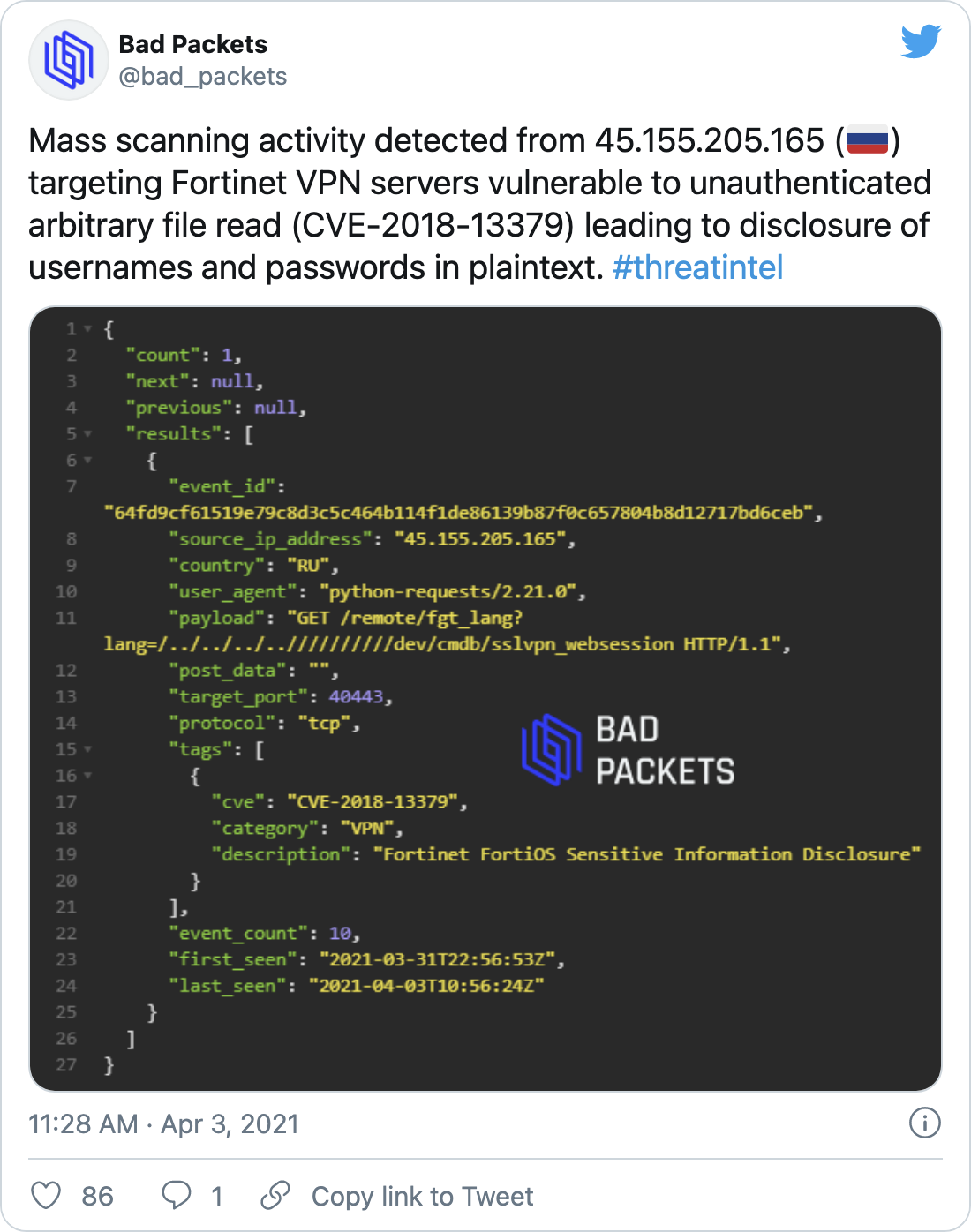
CVE-2018-13379, CVE-2019-5591, CVE-2020-12812: Fortinet Vulnerabilities Targeted by APT Actors - Blog | Tenable®

The Top 10 Most Exploited Vulnerabilities: Parsing an Important Recent National Cyber Awareness System Alert -- Security Today

The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog
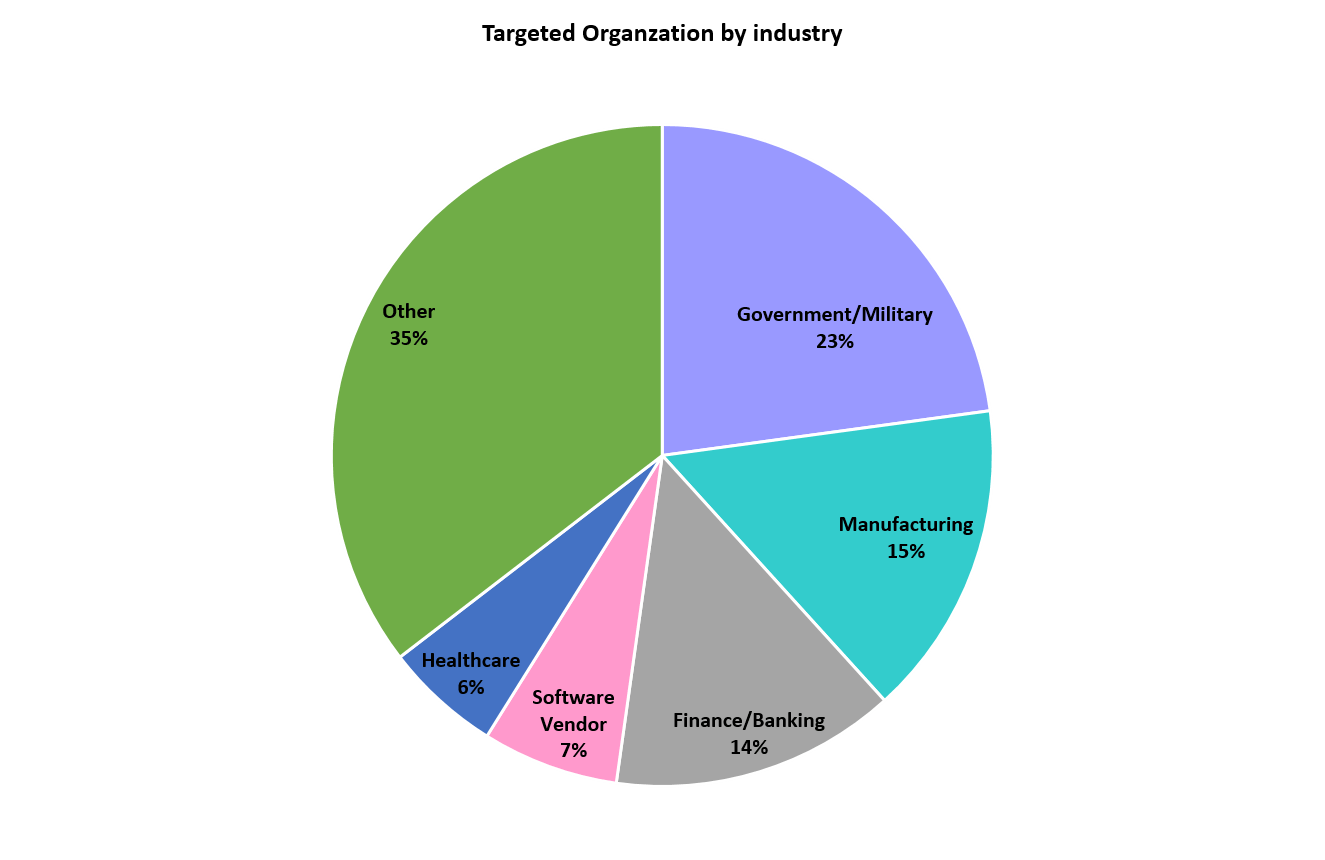
Exploits on Organizations Worldwide Grow Tenfold after Microsoft's Revelation of Four Zero-days - Check Point Software